Our Vision
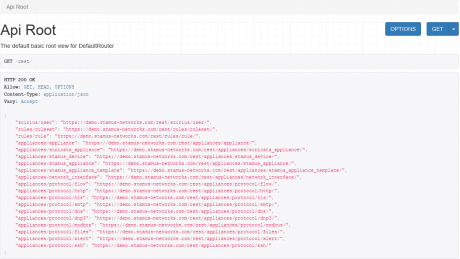
Stamus Networks believes in the power of correlated data to enable security practitioners to find intrusions within their network. This belief has driven us to marry a custom network traffic analysis engine with a powerful intrusion detection engine. We then added a purpose-built threat hunting interface to easily search through diverse, contextual data across domains, network segments, user agents, host IDs, IDS events and other perspectives. Moreover, through an extensive RESTful API and the introduction of Run Your Own Defense (RYOD) containers, Scirius Enterprise enables the integration of its broad scope of network data into your security ecosystem to maximize the overall investment into your security practice.
Scirius Enterprise
Network Traffic Analysis
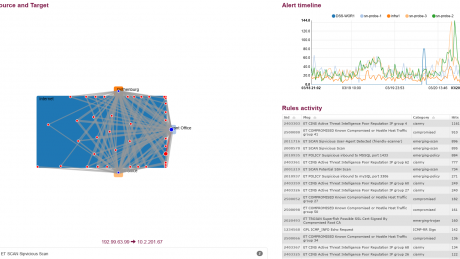
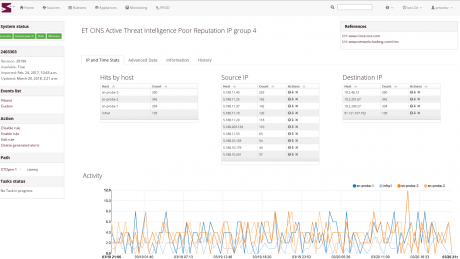
We call it Information Flow Security Awareness (IFSA). Scirius Enterprise produces security and alert trends across networks, segments of networks and sites in chronological order. The solution empowers analysts with the visualization of lateral movement which is also infused into the rich and comprehensive metadata that has drawn top-tier security practitioners to Stamus Networks. The solution simplifies sometimes confusing source and destination IPs by illuminating the target to speed investigations. Logging of HTTP, DNS, TLS and SMB (among other protocols) is further enhanced with host fingerprinting as well as identifying fully qualified domain names. Scirius Enterprise leverages advanced analytics from Stamus Networks and rule-based detection to expose suspicious activities on enterprise networks.
Advanced Cyber Threat Hunting
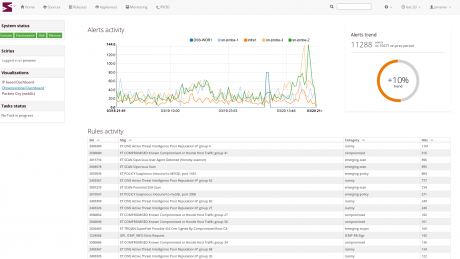
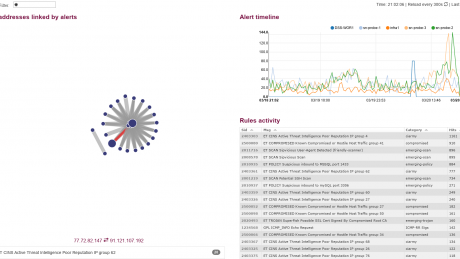
Today’s threat landscape requires proactively searching for bad actors in your network that have circumvented preventative measures within your enterprise. According to the Ponemon Institute, the average company takes 170 days to detect an advanced threat, 39 days to mitigate, and 43 days to recover from a breach. Cyber threat hunting is anything but an exact science. The proactive pursuit of threat actors is a process that requires the ability to search and display data in a dynamic way and pivot from one perspective to another based on indications of compromise that stand out in each subsequent search. Scirius Enterprise provides heightened situational awareness driven by Stamus Networks analytics and the agnostic ability to incorporate multiple threat intelligence sources.
Intrusion Detection
Intrusion detection systems (IDS) are required by security compliance standards such as PCI, GDPR, HIPAA, SOX and many others. Having an IDS within your security stack is considered best practice. Yet the capabilities of legacy IDS solutions have remained stagnant and they have largely lost relevance in the overall IT security ecosystem.
Scirius Enterprise is driving a paradigm shift in network security in two ways. First, we don’t just manage the noise but turn it into useful insights with automated classification, advanced tagging and high-value event filtering. Secondly, by correlating IDS events with network traffic analysis results, Scirius provides a view into your network that neither a network traffic analyzer or a standalone IDS can provide.
Scirius Enterprise is the tool of choice for top-tier practitioners and a categorical enabler of Tier 1 analysts. Isn’t it time to make your IDS useful?
Contact us
Stamus Networks is a global company with headquarters in Indiana:
Stamus Networks LLC
14807 Newpot Dr
Westfield, IN 46074
United States
Stamus Networks SAS
44 rue Bayen
75017 Paris
France
If you have a question, would like more information about Stamus Networks, our technology or our products and services, please fill in for following form and someone will contact you shortly.
[hubspot type=form portal=6344338 id=969cf449-2f1c-4c6c-b30e-b416ab419e70]